As organizations increasingly move their workloads to the cloud, managing who has access to what becomes a critical pillar of governance and security. Oracle Cloud Infrastructure (OCI) addresses this need with its powerful Identity and Access Management (IAM) service.
In this post, we’ll explore the fundamentals of OCI IAM, its key components, and how it helps maintain secure, scalable access control in a cloud environment.
What Is OCI IAM?
IAM (Identity and Access Management) is a foundational OCI service that lets you control access to cloud resources. It allows you to define:
- Who can access your OCI environment
- What actions they can perform
- Which resources they can interact with
This access control is implemented through authentication (AuthN) and authorization (AuthZ):
- Authentication (AuthN): Verifies the identity of a user or system
- Authorization (AuthZ): Determines what actions they are permitted to perform
Core Components of OCI IAM
OCI IAM includes a rich set of features for defining identities and controlling access:
✅ Identity Domains
An identity domain is a logical container for users, groups, and related configurations. It defines the user population and their authentication settings, similar to a directory service.
✅ Users and Principals
- Users represent individual human users or system accounts.
- Principals can be IAM users or resource principals (services using OCI resources).
✅ Groups and Dynamic Groups
- Groups are collections of users who share the same access requirements.
- Dynamic Groups are rule-based groupings where membership changes automatically based on defined conditions (e.g., instance OCID, tags, etc.).
✅ Policies
OCI policies are written in a human-readable format and define authorization rules for users and groups. Policies always allow actions—OCI follows a default deny and least privilege model.
✅ Compartments
A compartment is a logical grouping of related cloud resources. When you create an OCI account (tenancy), you get a root compartment. Best practice, however, is to organize resources into dedicated compartments (e.g., for networking, storage, compute) to enhance access control and isolation.
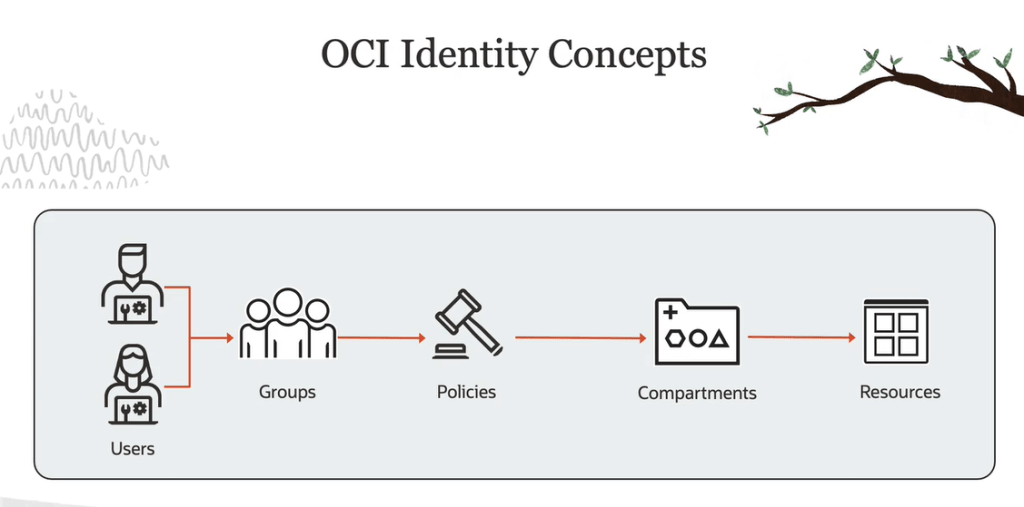
IAM Policy Structure and Syntax

OCI policies follow a clear, modular syntax:
plaintextCopyEditAllow <subject> to <verb> <resource-type> in <location> [where <conditions>]
- Subject: Group(s) or dynamic group(s)
- Verb: Action type (inspect, read, use, manage)
- Resource Type: OCI service (e.g.,
vcns,volumes,virtual-network-family) - Location: The compartment or tenancy in which the policy applies
- Conditions: Optional expressions to enforce contextual constraints (e.g., based on IPs or tags)
⚠️ If you omit the identity domain in the subject, OCI assumes it belongs to the default domain.
Advanced Features and Federation
OCI supports federation with third-party identity providers (IdPs) like Microsoft Entra ID (Azure AD), allowing enterprises to delegate user and group management to external directories while using OCI policies to define access control.
Additionally, Network Sources can be defined as sets of IP addresses or CIDR blocks, and used in policies to allow or restrict access based on network origin.
Best Practices for IAM and Compartments
- Use compartments to segment resources logically by department, function, or lifecycle.
- Avoid assigning policies directly to users—use groups and dynamic groups instead.
- Follow the principle of least privilege by granting only necessary permissions.
- Federate identity with enterprise IdPs to centralize user management.
- Leverage network-based access control using network sources in advanced policies.

Conclusion
OCI Identity and Access Management is a powerful service that provides fine-grained control over user access and resource authorization. By leveraging its features such as identity domains, dynamic groups, and compartment-based isolation, organizations can enforce security best practices while scaling confidently in the cloud.
Whether you’re just getting started with OCI or looking to refine your access strategy, understanding IAM is essential to building a secure and well-governed cloud environment.

Leave a comment